Introducing Trustworthy
We’ve all seen the tense scene in a war movie where the order has come down to launch the nuclear missiles. The captain and his first officer each take out a special key they’ve had around their neck the whole time. Then they both insert their individual keys into the weapons computer and turn simultaneously. Despite being a popular motif, this is a real policy implemented by many military organizations, including the U.S. Air Force. Once you think about it this kind of policy is obvious, one person shouldn’t be able to launch nuclear weapons on their own. Trustworthy is like having a two-man rule for your data.
How it works
Trustworthy is implemented as a ruby gem with the source on GitHub. When installed via ruby gems it creates a new command line utility named trustworthy.
Once you have installed trustworthy, the first step is to generate a new master key. This key is never stored anywhere on disk but is instead derived from at least two user keys.
$ trustworthy init
Creating a new master key with 2 keys
Username: user1
Password:
Password (again):
Key user1 added
Username: user2
Password:
Password (again):
Key user2 added
Created trustworthy.yml
This command will generate the key in the background and then split it using Shamir’s Secret Sharing Algorithm. You can then use trustworthy to encrypt and decrypt files using this master key.
$ trustworthy encrypt secret.txt
Username: user1
Password:
Unlocked user1
Username: user2
Password:
Unlocked user2
Reconstructed master key
Encrypted secret.txt to secret.txt.tw
Additional users can be added provided two current users unlock the master key to do so.
$ trustworthy add-key
Adding a new key to master key
Username: user1
Password:
Unlocked user1
Username: user2
Password:
Unlocked user2
Reconstructed master key
Username: user3
Password:
Password (again):
Added user3
Shamir’s Secret Sharing Algorithm
The algorithm behind trustworthy is incredibly simple and requires nothing more than a high school understanding of algebra. Trustworthy uses Shamir’s Secret Sharing algorithm to split a master key between two users. In general, Shamir’s Secret Sharing algorithm uses a polynomial as the master key. Each user is given a unique point along that polynomial that can be used to reconstruct the master key at a later point. Trustworthy implements the most basic form of Shamir’s Secret Sharing algorithm, polynomials of degree one.
If you think back to high school you might remember the slope intercept form y = mx + b which defines a line. The y-intercept, b, is used by trustworthy as the master key.
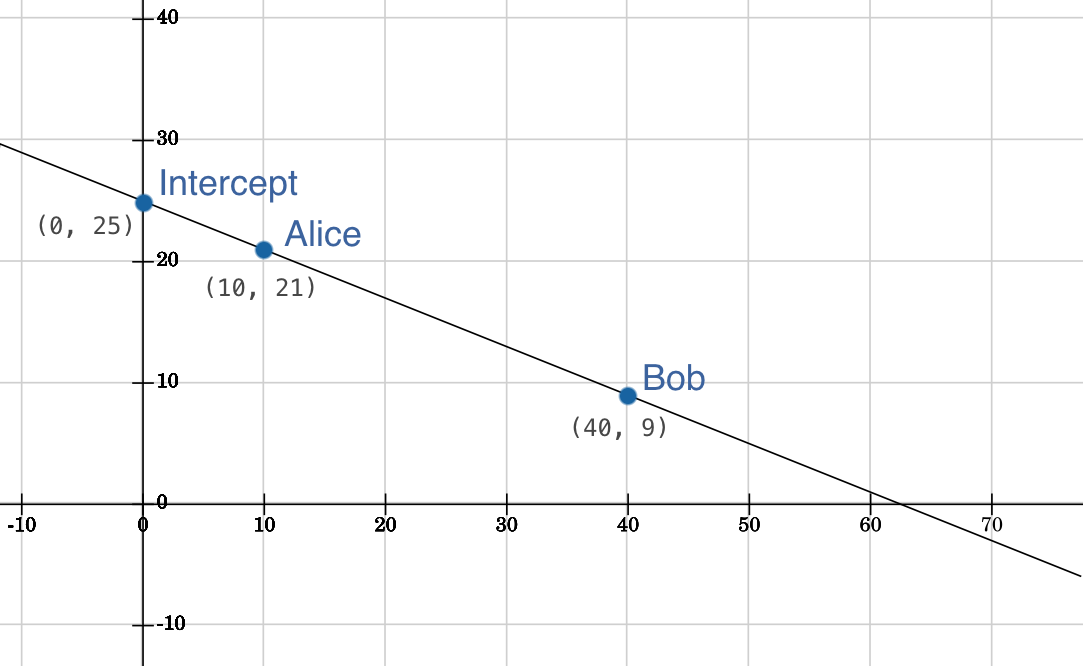
In this example, Alice is given the point 10, 21, and Bob is given 40, 9. By themselves, neither Alice nor Bob can figure out the y-intercept. However, once they come together, they can recompute the line and easily derive the y-intercept 40. To protect the points along of the line, trustworthy encrypts the data using a user supplied password. At runtime the user provides the password so that the point can first be decrypted.
Contributing
If you think of a new feature or happen to find a bug feel free to open an issue on GitHub.